Bypassing MFA for an email parser user
Introduction
OAuth 2.0 does not work with MFA when the application type is a background service with no manual interaction. MFA is built for manual user interaction to provide MFA code and authenticate.
Steps
For the users who are concerned about bypassing the MFA for the email parser, they can simply do it by IP address. Only requests coming from the BMS servers with OAuth token requests can bypass MFA, and this will remove the concerns. This can be done as follows:
- Log into Microsoft admin portal (https://admin.microsoft.com/adminportal/home/).
- Click Users > Active Users.
- Next, click Multi-Factor Authentication.
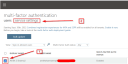
- Select the user whose MFA is enabled and then click service settings. You will be taken to a different page.
- Under Trusted IPs, click in the text box and type the IP address or range of addresses that you want to exclude from MFA based on the BMS server used.
- US BMS (bms.kaseya.com) IP address: 52.144.52.4/32
- UK BMS (bmsemea.kaseya.com) IP address: 139.28.145.11 and 139.28.145.125
- APAC BMS (bmsapac.kaseya.com) IP Address: 13.55.204.127/32
- Vorex (vorexlogin.com) server IP address: 52.144.52.4/32
- This way you will be able to set up the email parser for the O365 account which is enabled with the MFA.
- Click Save.
Microsoft Entra Conditional Access
For information on conditional access, see Microsoft Entra Conditional Access.



